Overview
Setting Up
Command Line Options
The Config File The Rules File
- Interface Tests
- Ethernet Tests
- IP Tests
- ICMP Tests
- TCP Tests
- UDP Tests
- TCPStream Tests
- DNS Tests
- HTTP Tests
- Includes
| Setting up a Bait&Switch Honeypot |
Bait&Switch Honeypots are a production Honeypot designed to let you observe attackers in a safe enviroment. The Bait&Switch code is experimental and may change in the future.
To set up a Bait&Switch Honeypoet, you'll need a box with 3 Network Cards:
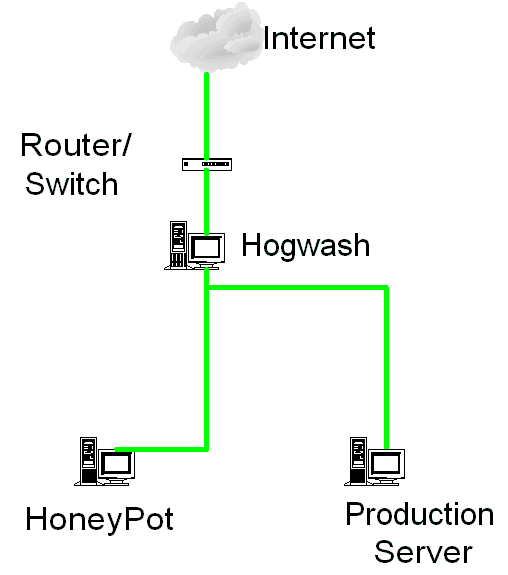
The Production Server is the box you're trying to protect. It has all your credit card numbers an other goodies on it. The HoneyPot is where you're going to let the attackers play and watch them.
When Hogwash detects an attacker, he'll be switched from the production server to the HoneyPot. If the attacker notices he's been switched, he'll probably go away (which is good), but if he doesn't you can watch what he was going to do to your production server (which is better).
Both the production server and the HoneyPot need to have the same IP address. You can set them up to have the same MAC address as well, but it's not required. You should mirror the content of the production server onto the honeypot regularly.
The setup has been simplified in the latest release. You need to add the following sections:
<IPList GreenList>
10.3.3.3/32
</list>
<IPList BlackList>
192.168.0.1/32
</list>
<Action RouteMe>
response=alert console
response=alert file(hogwash.alert)
response=dump packet(packet.log)
response=bns(3600, GreenList)
</Action>
<routing>
bns(eth0,eth1,eth2,BlackList)
</routing>
GreenList is a list of IPs never to reroute to the HoneyPot. BlackList is a list of IPs to always route to the HoneyPot.
The format of the bns action is bns(<timeout>, <GreenList>). If timeout is set to -1, the reroute will not timeout.
The format of the bns routings is: bns(<InternetIF>, <ProductionIF>, <HoneyIF>, <BlackList>)
If you have more than one production server and honeypot, you don't need to add any additonal lines. Hogwash will automatically detect the HoneyPots and rout accordingly.
There will be a several second delay after you start up Hogwash until packets will flow on the network. Hogwash uses ARP packets to discover the production and HoneyPot machines. The HoneyPot isn't allowed to talk until there is a produciton machine with the same IP.
That's about all there is to it. Have Fun.